Oscar De La Renta Intrusion by Oscar De La Renta Set (w) 085715581464 - Fragrances & Beauty, Fragrances - Jomashop

Mekong Delta sets up public tap water faucets as saline intrusion peaks | Society | Vietnam+ (VietnamPlus)

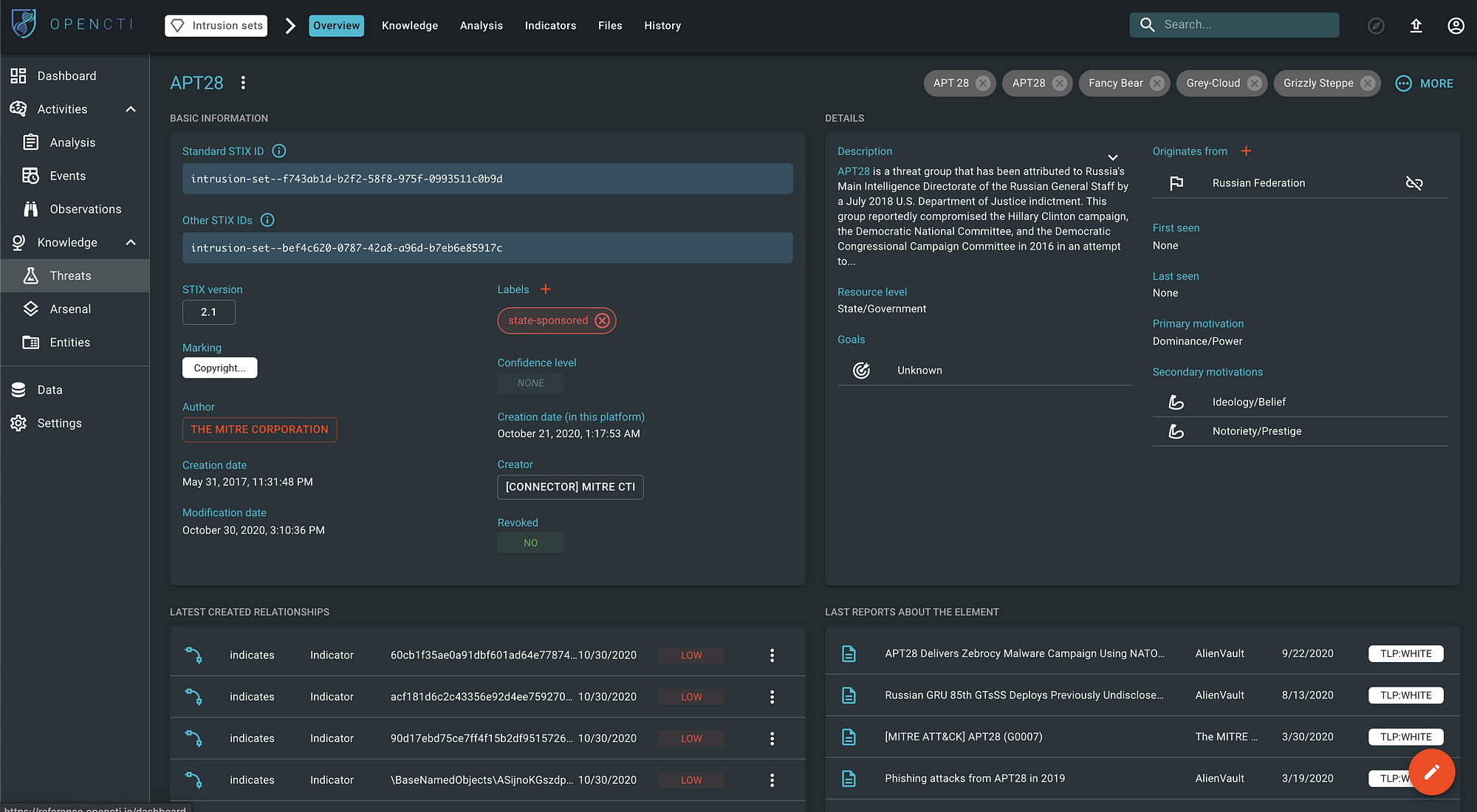
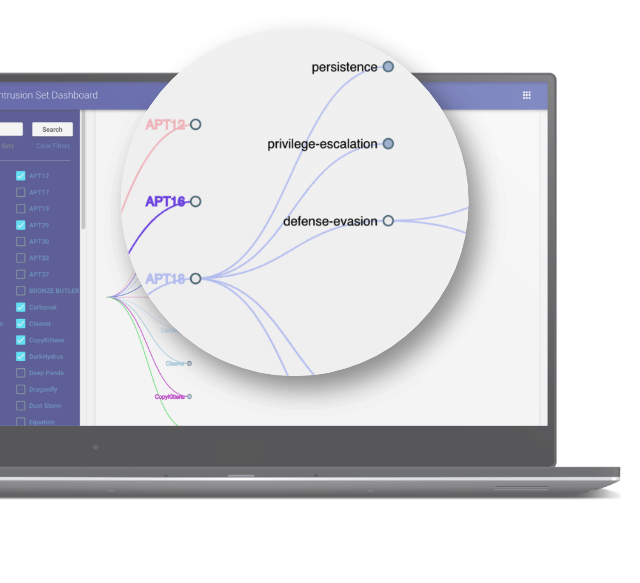
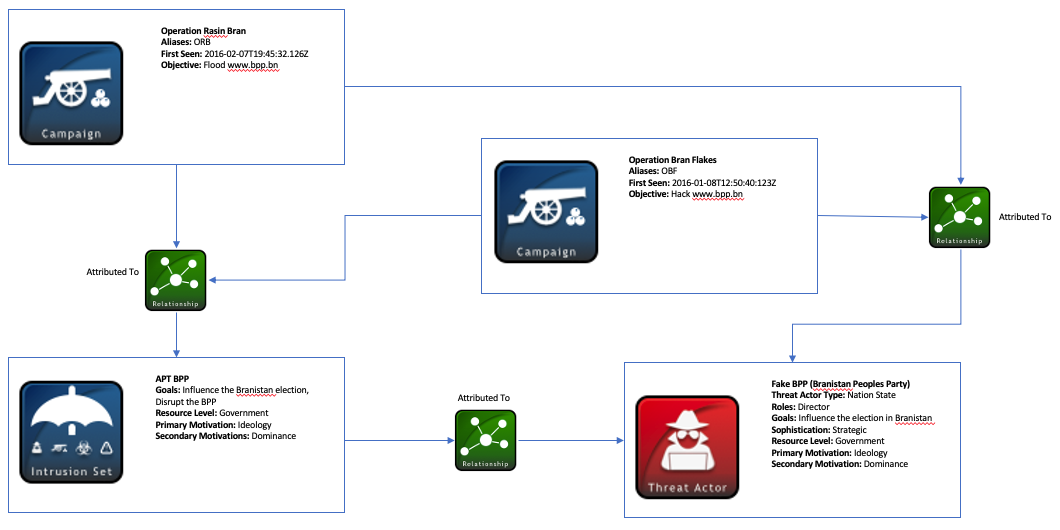
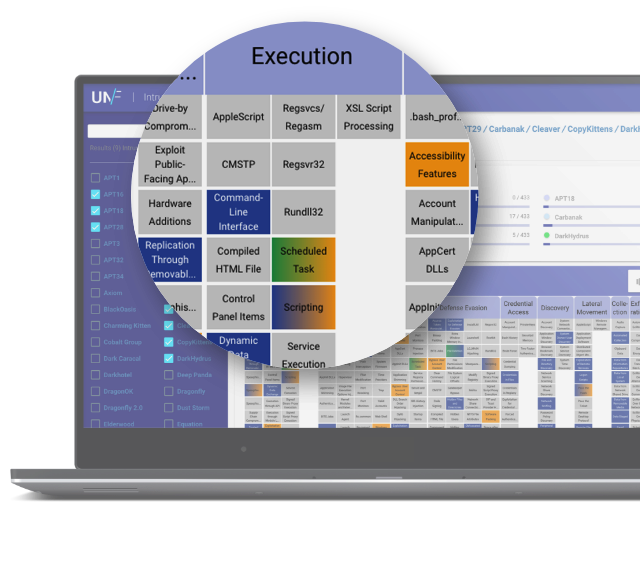
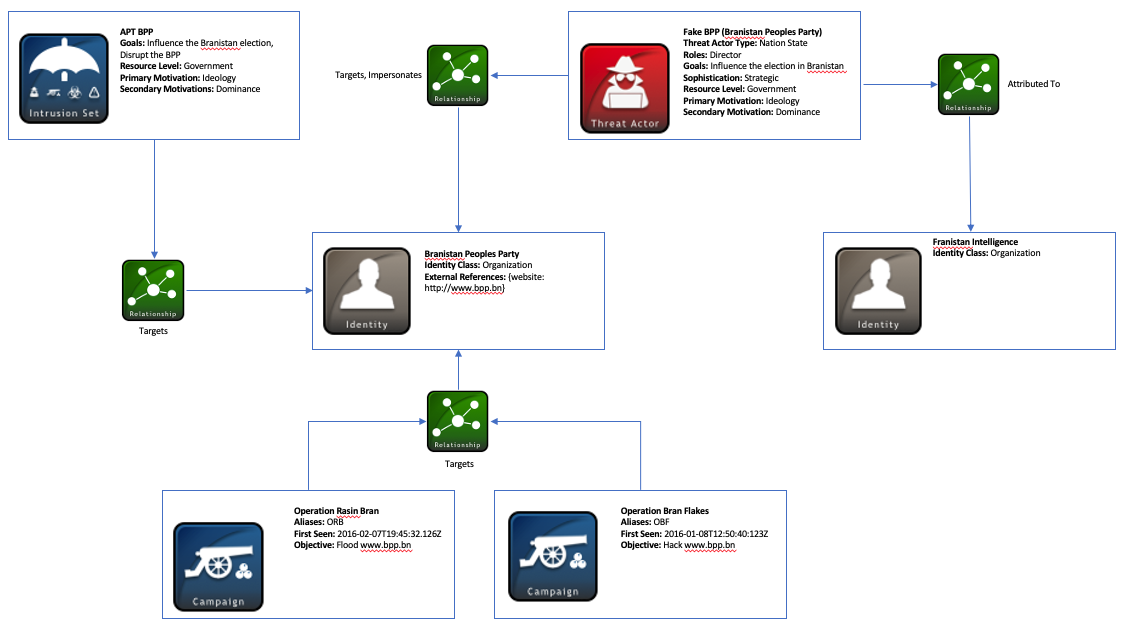
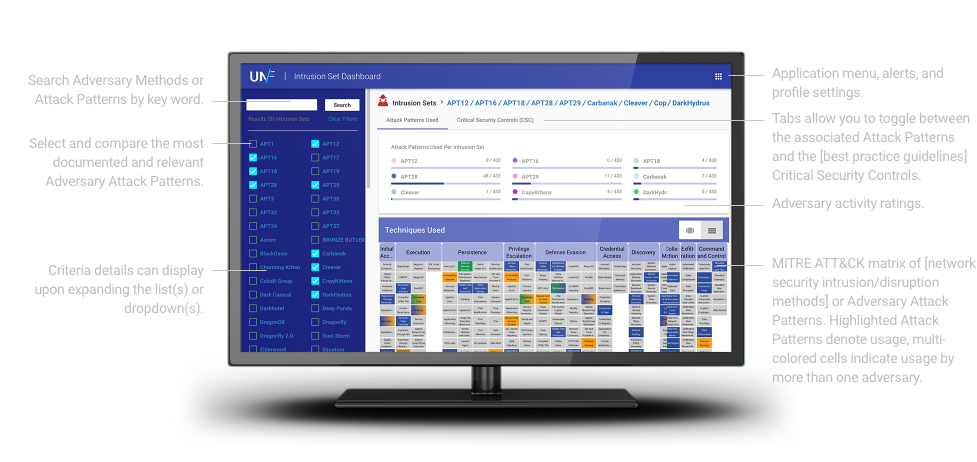
Managing Cyber Threat Intelligence in a Graph Database: Methods of Analyzing Intrusion Sets, Threat Actors, and Campaigns | Semantic Scholar

i) Overall work flow of the proposed intrusion detection system using... | Download Scientific Diagram